 Look beyond What You See: Transformation Based Privacy-Preserving Data Analytics and Utilization in Wireless Networks
Look beyond What You See: Transformation Based Privacy-Preserving Data Analytics and Utilization in Wireless Networks
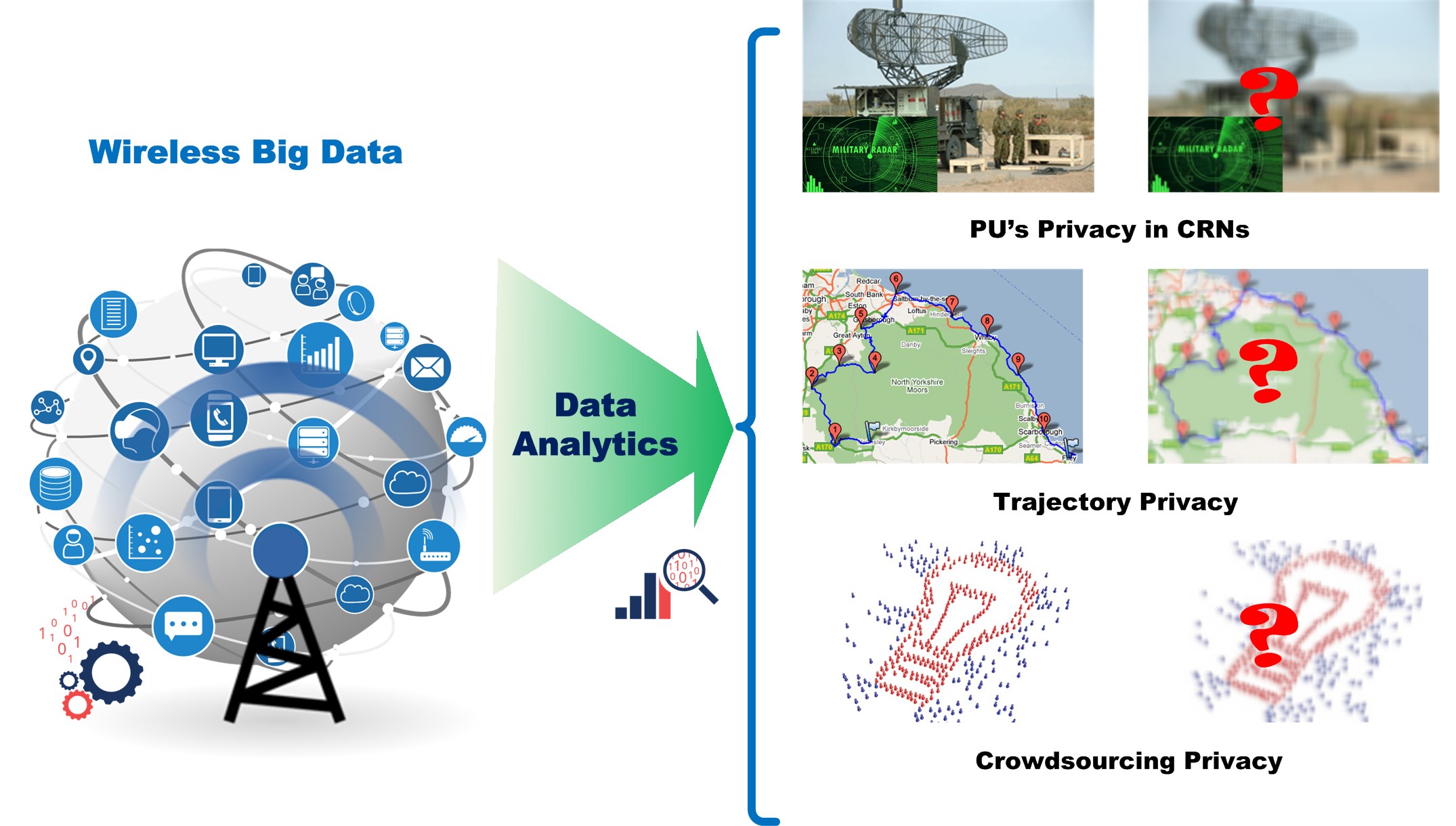
With the proliferation of sensor-rich mobile devices like smartphones, and wireless networks such as cognitive radio networks and mobile social networks, wireless data traffic is surging and has become a major source of big data nowadays. Wireless big data has created enormous value using data analytics in terms of enabling numerous mobile applications and improving wireless communication services. Meanwhile, a lot of sensitive personal/operational information about the involved participants can be inferred from the wireless data, compromising their privacy. The goal of this project is to build a framework for privacy-preserving data analytics and utilization in wireless networks, which allows enjoying the benefits brought by the wireless big data while protecting the privacy of participants. Ideally, useful information can be extracted to the maximum extent, while sensitive information about participants is perfectly protected from their data. If that is impossible to achieve, this project proposes to leverage data transformation paradigms to optimize the trade-off between participants’ utility and privacy protection in different wireless networks.
 Secure and Efficient Maritime Data Storage and Retrieval
Secure and Efficient Maritime Data Storage and Retrieval
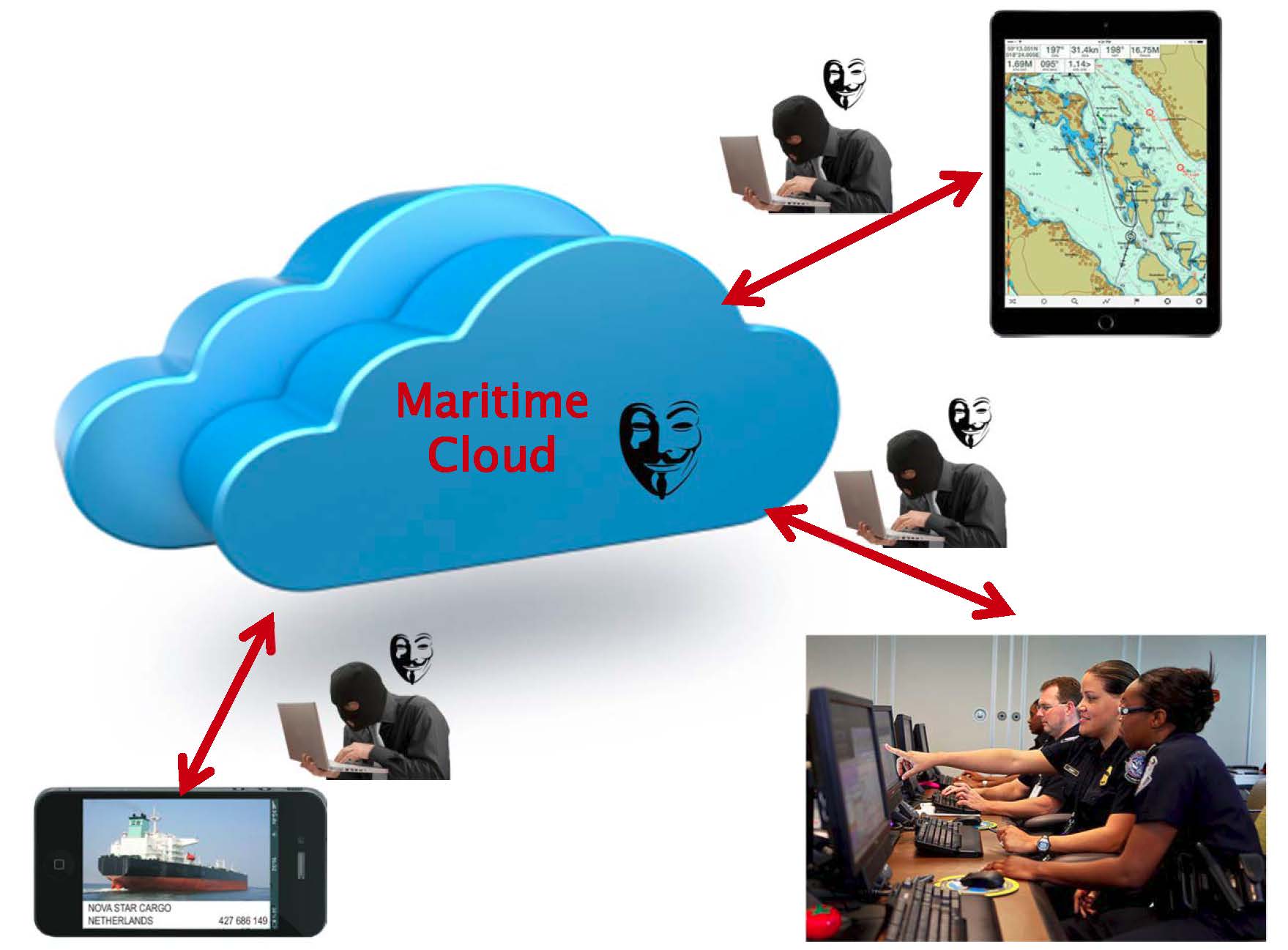
Due to the massive amount of maritime cargo containers entering U.S. ports, it costs too much to store all the cargo records in their local servers at local ports (e.g., the cost of adding servers, data maintaining cost, the cost of server specialists, etc.). To effectively reduce the cost, it will be a promising idea and a trend to push all the maritime data into the large data centers, i.e., the cloud. Since the maritime data is sensitive, this project will develop encryption schemes to keep the data integrity and make sure the data cannot be amended by the malicious attackers. Meanwhile, since maritime data is frequently updated/stored and retrieved, this project will also employ cryptography techniques to secure efficient data storage and retrieval. The attack model will be investigated, security analysis and complexity analysis will be conducted for the proposed schemes, and the results of this research will help to secure efficient maritime data storage and retrieval.

